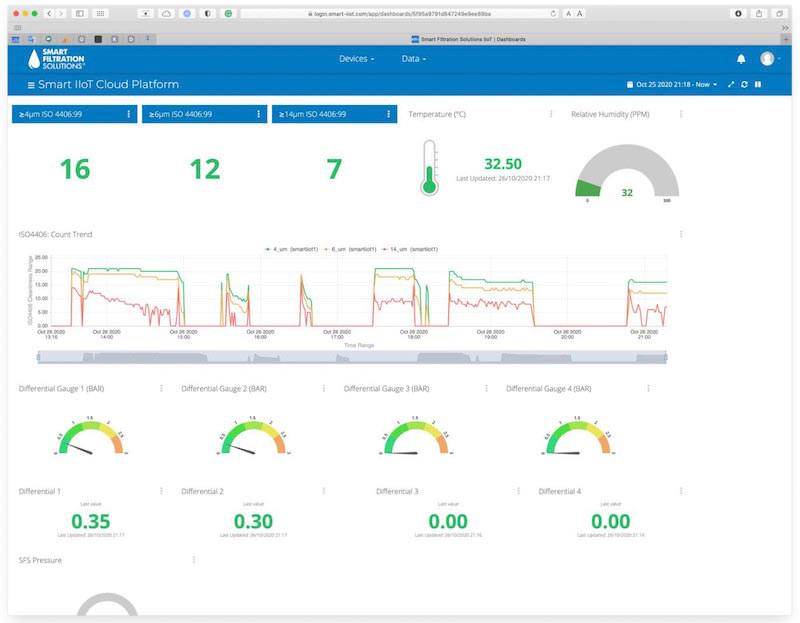
Smart-IIoT provides easy access to cloud storage for viewing dashboards and reporting tools. All of this data is stored in the cloud via WiFi, LAN or 2G/3G/4G connection where it is presented it our customers on our web portal on their computers, tablets or smart devices. Alerts and warning levels can be set, so our customers can act on issues as soon as they occur.
Smart-IIoT provides an excellent opportunity for our customers to analyze historical data trends to help determine more effective maintenance procedures, set user-programmable alarms for different site requirements.